Information on buying a car including finance and vehicle inspections. Join the fight against malicious programs and cybercrime on our Computer Science Cyber Security MSc.
As of May 2014 the Internet is delivered to India mainly by 9 different undersea fibres including SEA-ME-WE 3.

. What are the Categories of Cyber Crime. There are different types of cyber crimes that use malicious code to modify data and gain unauthorized access. In the course of 2022 the Health Protection Command of the Carabinieri Corp enforced 61 orders issued by the competent directorates general of the Ministry of Health providing for the shutdown of websites selling different types of prescription-only medicines in breach of the existing legislation.
Human trafficking slavery and slavery-like practices such as servitude forced labour and forced marriage are complex crimes and a major violation of human rights. As a leading voice in the fight against cybercrime we work tirelessly to discover key insights that allow us to protect 500K companies worldwide from 100s of millions of threats daily. A Offenses against the confidentiality integrity and availability of computer data and systems.
Banco de sabadell sa. Bigpay malaysia sdn bhd. Banco de la nacion.
However it could result in unfairness if 2 two different statutes apply to the same. Cybercrime presents a major risk to prosperity in the global digital economy. There are subtle differences in punishments under these statutes especially in aspects like whether the offence is bailable or compoundable or cognizable.
Historically ransomware has targeted a number of high-value sectors finance professional services the public sector in wealthy countries concentrating on the US and other G7 membersRecent attacks on countries such as Costa Rica South Africa. Gaborone University College Botswana. If you feel you have been scammed by a person claiming to be a US.
College of Allied Educators Singapore. Cybersex trafficking is distinct from other sex crimes. Victims are transported by traffickers to.
An amendment of the Constitution can be initiated only by the introduction of a bill for the purpose in either House of Parliament Lok Sabha Rajya Sabha and not in the state legislatures. Enterprises need help to stay ahead of both simple ransomware attacks and advanced rapidly evolving cybercrime operations. Saigon thuong tin commercial joint stock bank.
Section 4a3 of the Cybercrime Law Section 4a3 provides. The British College Nepal. They also have the opportunity to study crime prevention methods in depth and acquire knowledge of different types of crime such as cybercrime or organised crime.
Click on a tile below to get started. Management Development Institute of Singapore Singapore. Therefore you will not encounter cyber-crime activity with your A9-Wallet and luckily there are no incidences of fraud that have been reported since we developed the A9Play gambling site.
Full list of international. We specialise in managing risk. Study Undergraduate Postgraduate and Continued Professional Development CPD courses in Leeds for students graduates and business.
Types of scams and cybercrime how to report them getting help and tips to stay safe. Types of Amendments Constitutional Amendment Process. X x x x 3 Data Interference.
Asian Institute of Built Environment Hong Kong. We understand the threats that your business may face. To enhance the value that you deliver to your stakeholders we can assist you in protecting your business and its success.
Cars other vehicles. Advertising is an effective way to attract customers but the law says advertising must be truthful and easy to understand. Streamline access to every cloud application that employees need to get the job done with individual employee Launchpads.
Around the world men women and children are trafficked for a wide range of exploitative purposes such as. An offence such as obscenity may take place through different types of media both online or offline. The hacker group Russian cybercrime syndicate Evil Corp was thought to be behind this attack.
A spate of ransomware targeting countries in the Global South has demonstrated an evolution in attackers tactics. Protect yourself against business threats. They will develop a broad knowledge of the field of security and crime science and a familiarity with the latest academic research through studying with world-leading experts.
From the global banking crisis to the rise of cybercrime recent history demonstrates the importance of identifying threats. Cyber crimes are categorized into three broad categories individual property and government. The bill can be introduced either by a.
Servitude Slavery Forced labour Debt Bondage Forced marriage or Organ harvesting Australia is. General public access to the internet began on 15 August 1995 and as of 2020 there are 71874 million active internet users that comprise 5429 of the population. Internet in India began in 1986 and was available only to the educational and research community.
Vietnam technological and. The procedure for the amendment of the Constitution as laid down in Article 368 is as follows. Media reports stated that CNA Insurance agreed to pay 40 million as ransom to get back access to its network.
Based on each category of cyber crime cybercriminals use different levels and types of threats. Soldiers currently serving in Iraq. The A9Play app employs A9-Wallet with a built-in latest security system technology to secure your account against fraud hacking and other types of cybercrime.
Cybersex trafficking live streaming sexual abuse webcam sex tourismabuse or ICTs Information and Communication Technologies-facilitated sexual exploitation is a cybercrime involving sex trafficking and the live streaming of coerced sexual acts andor rape on webcam. Hong leong bank berhad. Soldier contact the FBI Internet Crime Complaint Center and the Federal Trade Commission.
The following acts constitute the offense of cybercrime punishable under this Act. Banque al wava mauritanienne. Secure Password Vaults.
Gathering the latest threat intelligence from around the world Trend Micro Research continuously explores the threat landscape to bring you the trusted insights you need to withstand threats now and in. Buying selling a car. Store all your passwords.
Third-party forensic experts revealed that they had created and used a new form of ransomware called Phoenix CryptoLocker for this attack. This must-have stops more than 90 of password-based cybercrime. First national bank of swaziland.
Find a course at Leeds Beckett University. Almost 11500 cyber events were reported to Switzerlands National Cyber Security Centre in the second half of 2021 alone and they are growing more sophisticated said Roger Albrecht co-lead ISG Cybersecurity. With Passly users can securely access any tool including productivity CRM ticketing HR and more.
Online Romance Scam Information. Hong Kong College of Technology Hong Kong. The intentional or reckless.
Rushmore Business School Mauritius. We will give you the skills you need to become a Cyber Security and Digital Forensics professional intercepting collecting analysing and reporting the events in cyberspace and digital media. To systematically address this threat it is imperative to raise the cost of conducting cybercrime and increase the risks for cybercriminals.
This can only be achieved through effective public-private cooperation with global businesses and other cyber responders working side by side with law. Army CID is warning anyone who is involved in online dating to proceed with caution when corresponding with persons claiming to be US.

Cybercrime Legislation Cases And Commentary 2nd Edition Lexisnexis Australia

What Is Cybercrime Different Types And Prevention

Types Of Cybercrime Panda Security Mediacenter

Zeus Malware Double Threat How To Defend Yourself Against Zeus P1networks More Info Https Storify Com P1ne Malware Cyber Security How To Defend Yourself

Types Of Cybercrime Panda Security Mediacenter
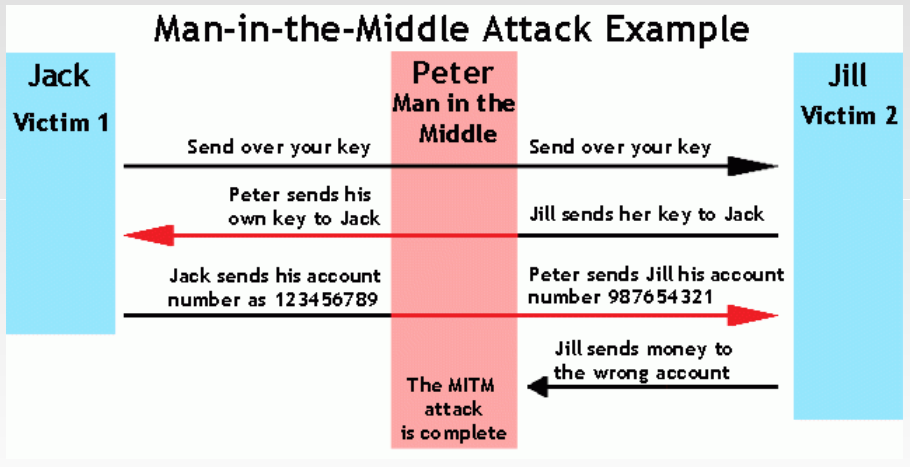
Cybercrime Module 2 Key Issues Offences Against The Confidentiality Integrity And Availability Of Computer Data And Systems
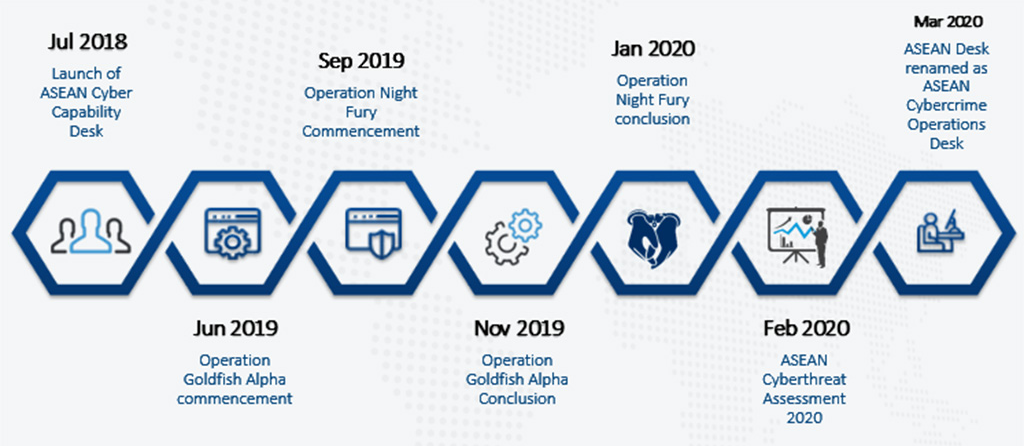
Asean Cybercrime Operations Desk

4 Cybercrime Investigation Framework Download Scientific Diagram

Cybercrime Vs Traditional Crime Techniques A Comparison

Cybercrime Definition Types And Reporting Clearias

Cybersecurity Main And Emerging Threats In 2021 Infographic News European Parliament

This Infographic Shows The State Of Encryption Today Encryption Infographic Infographic Encryption

Cybercrime In India Surges Amidst Coronavirus Lockdown
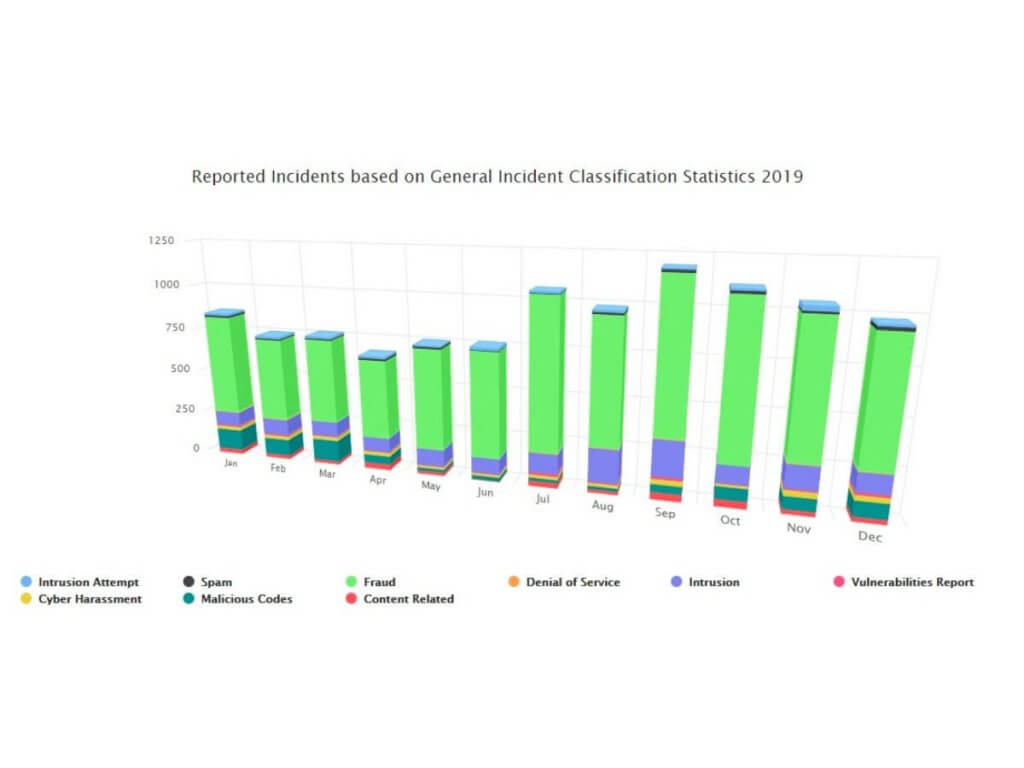
The True Cost Of Cyber Crime In Malaysia Spectrum Edge

How Common Is Cyber Crime In Australia Ecu Online

The 10 Worst Cyber Crimes Analysed

Cybercrime Emergence Types And Some Mitigating Steps
Cybercrime Which Ones Are The Most Common Threats Today Red Points


